Cybersecurity is more important than ever, yet many organizations overlook one major vulnerability—security misconfiguration. These preventable errors can open the door to devastating attacks.
The Open Web Application Security Project (OWASP) updated its famous list of top 10 vulnerabilities in 2021, with security misconfiguration ranking as the 5th most dangerous risk.
If you’ve ever wondered what a security misconfiguration is and how it impacts your business, you’re in the right place. Let’s explore the dangers and steps you can take to protect your organization.
What is a Security Misconfiguration?
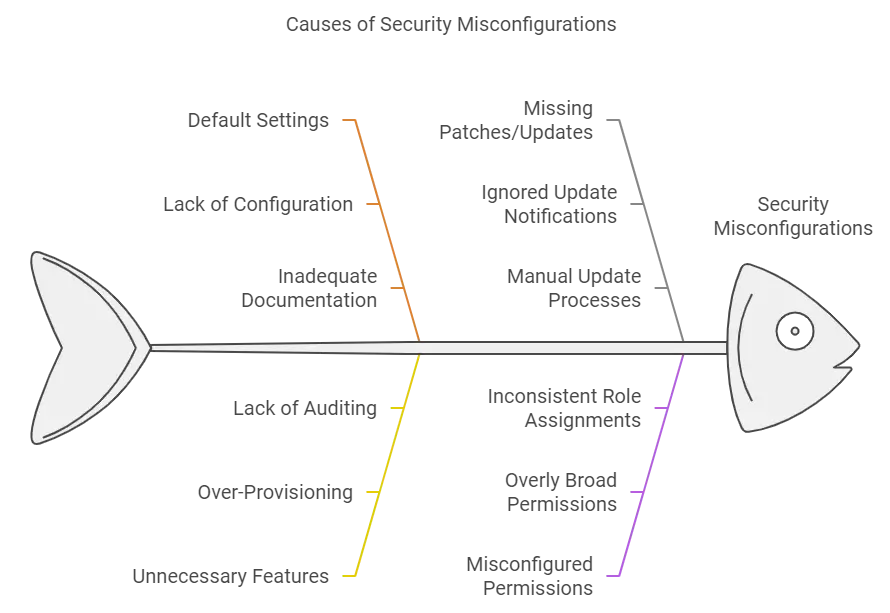
At its core, a security misconfiguration occurs when security settings are improperly configured or left at their default values. These missteps leave systems vulnerable to cyberattacks. It could be something as simple as failing to remove default credentials or leaving unnecessary features enabled on servers.
These simple mistakes often create large gaps in your security, making it easier for attackers to exploit security misconfiguration vulnerability.
Common Types of Security Misconfigurations
1. Default Configurations
One of the most common misconfigurations is leaving default settings untouched. Default passwords, ports, or configurations are widely known, giving attackers a straightforward entry point. Always update and customize these settings.
2. Unnecessary Features and Services
Many applications or systems come with a range of services, features, or functionalities enabled by default. If these features are not used, they may become a security risk.
For instance, an application might have debugging or demo features turned on, or unused APIs exposed to the internet, which attackers could exploit. Disabling unnecessary features helps reduce the attack surface and limits potential entry points for attackers.
3. Improper Access Controls
Without proper access controls, sensitive data could be exposed. It’s essential to assign permissions carefully and limit access to only those who truly need it.
4. Unpatched Systems
Every day that a security patch isn’t applied increases your risk. Unpatched software remains one of the top reasons why security misconfiguration attacks occur. Make sure your system is up-to-date with the latest patches and security updates.
5. Incomplete or Missing Security Settings
Security tools can only protect you if they’re configured properly. Incorrect firewall or encryption settings can leave gaps in your defense, even if you’re using the right tools.
6. Misconfigured Permissions
Users or applications might have more access than necessary, allowing attackers to leverage excessive privileges to compromise systems.
7. Directory Listing Enabled
This setting reveals the structure of web directories, potentially exposing sensitive files that shouldn’t be visible.
8. Improper Error Handling
Detailed error messages might disclose information like database structures, server types, or configuration details.
9. Open Ports
Leaving unused network ports open invites attackers to explore and exploit potential vulnerabilities associated with those ports.
Real-World Security Misconfiguration Examples
Several major data breaches have occurred due to security misconfigurations. One of the most notable examples is the 2017 breach of Equifax, where unpatched software allowed hackers to access the personal data of over 147 million Americans. The financial and reputational damage was enormous, with fines and lawsuits costing the company over $700 million.
Another example is the Capital One breach in 2019, where a misconfigured firewall in a cloud environment exposed sensitive customer data. These cases illustrate the severe consequences of failing to address security misconfiguration vulnerability.
|
More articles you might like: |
Consequences of Security Misconfigurations
The consequences of security misconfigurations can be catastrophic:
- Data Breaches: Sensitive information such as financial data, personal details, or intellectual property can be exposed. According to an article by CloudSecureTech, on average, a data breach can cost a business millions, and sadly, 60% of small businesses have to close within six months after a cyber-attack.
- Financial Losses: Data breaches are expensive. The average cost of an organization detecting and escalating a data breach is $1.58 million.
- Reputational Damage: Customers lose trust in companies that cannot protect their data, leading to lost business opportunities.
- Legal and Regulatory Penalties: Companies can face steep fines if found in violation of regulations like GDPR or CCPA.
How to Prevent Security Misconfigurations
Now that you understand the risks let’s look at how you can prevent a security misconfiguration in your systems.
1. Conduct Regular Security Audits
Regularly review and audit your security settings to ensure they are properly configured. Don’t assume your systems are secure—verify it.
2. Apply Patches and Updates Promptly
Make patch management a priority. Set up automatic updates if possible, or ensure your IT team follows a strict patching schedule.
3. Disable Unnecessary Services
Reduce your attack surface by disabling services and features you don’t use. This minimizes the chances of these entry points being exploited.
4. Follow Security Best Practices
Utilize security frameworks such as the OWASP (Open Web Application Security Project) to guide your configuration processes.
5. Train Employees Regularly
Ensure that your IT staff and employees know the importance of proper configurations. Training should be a continuous process, especially as new tools and technologies are implemented. A Glance at Security Misconfiguration Prevention
| Misconfiguration Issue | Proactive Solution |
|---|---|
| Default Admin Credentials | Use strong, unique passwords |
| Unrestricted Access Permissions | Implement least privilege access controls |
| Lack of Secure Data Transmission | Enforce SSL/TLS for all data exchanges |
| Misconfigured Cloud Settings | Regularly audit cloud configurations |
| Missing Logging and Monitoring | Set up automated monitoring and alerts |
| Overly Permissive Firewall Rules | Regularly review and restrict firewall access |
Prosource – Your Partner in Preventing Security Misconfigurations
Security misconfigurations are a leading cause of cyberattacks, but they are preventable. By conducting regular audits, applying patches, and following best practices, you can minimize your exposure to security misconfiguration attacks.
Prosource specializes in helping businesses secure their systems and avoid these vulnerabilities. If you’re ready to protect your organization from misconfigurations, contact us today for a consultation.




